Cloud developers and IT teams struggle to stay ahead of challenges protecting users, data, and applications from today’s cybersecurity attacks. With Azure Firewall, network security policies can be enforced while allowing companies to take advantage of the scale and simplicity of Azure.
Azure Firewall:
The Azure Firewall is fully integrated with the Azure platform, portal UI, and services. It offers fully native firewall capabilities for all your virtual network resources, and it includes built-in high availability that lets you scale your resources automatically. Azure’s Network Security Groups (NSG) are able to allow/deny and filter TCP/UDP traffic.
How it works:
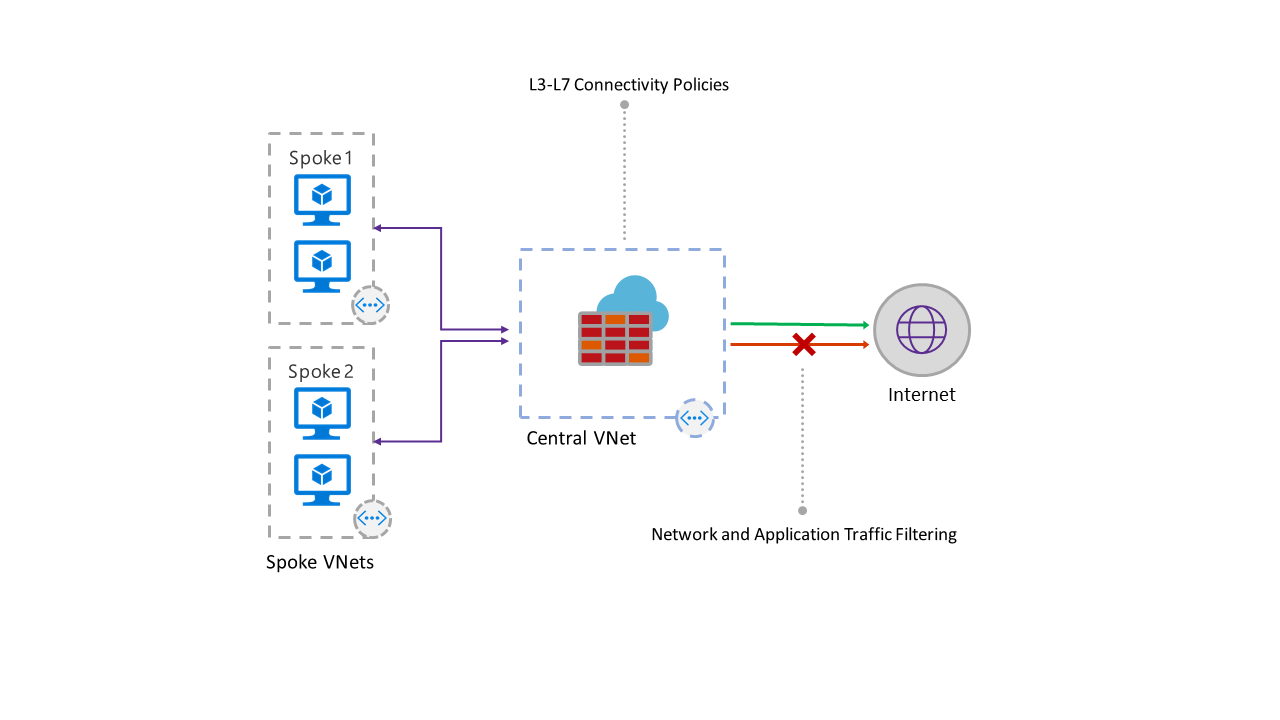
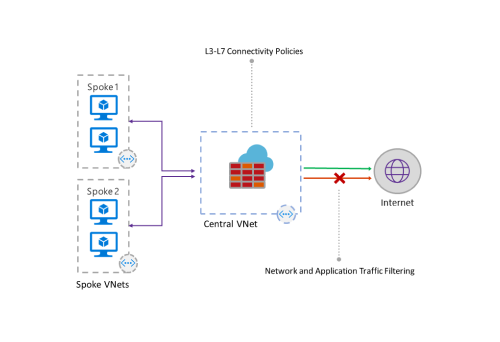
IT administrators can create connectivity policies using application and network filtering rules and enforce the policies across multiple subscriptions and virtual networks. The new service is built to work with Azure’s existing security services to strengthen and enhance the entire security experience.
Azure Firewall offers advantages like:
- Built-in high availability: No additional load balancers are required, and there is nothing you need to configure.
- Unrestricted cloud scalability: Azure Firewall scales automatically to accommodate changing network traffic flows, so IT administrators never need to budget for peak traffic periods.
- Application FQDN filtering rules: Users can limit outbound HTTP/S traffic to a specified list of fully qualified domain names (FQDN), including wild cards. This feature does not require SSL termination.
- Network traffic filtering rules: Centrally create “allow” or “deny” network filtering rules by source and destination IP address, port, and protocol. Azure Firewall is fully stateful, which enables it to distinguish legitimate packets for different types of connections. Plus, rules are enforced and logged across multiple subscriptions and virtual networks.
- FQDN tags: FQDN tags make it easy to allow well known Azure service network traffic through the firewall.
- Outbound SNAT support: All outbound virtual network traffic IP addresses are translated to the Azure Firewall public IP address (Source Network Address Translation). The firewall can identify and allow traffic originating from a virtual network to remote Internet destinations.
- Inbound DNAT support: Inbound network traffic to firewall public IP address is translated (Destination Network Address Translation) and filtered to the private IP addresses on virtual networks.
- Azure Monitor logging: All events are integrated with Azure Monitor, allowing IT administrators to archive logs to a storage account, stream events to Event Hub, or send them to Log Analytics.
For more information on Azure Firewall, contact SNP Technologies here.